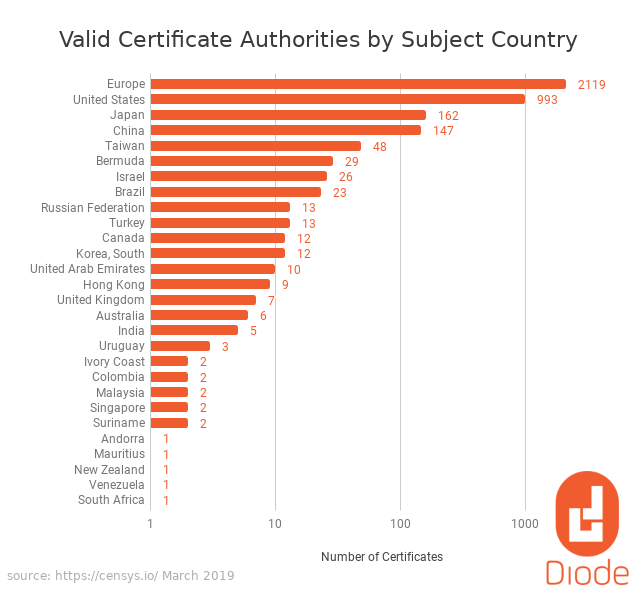
On Monday, Bleeping Computer published an article about the disturbing revelation that Dark Matter, a cybersecurity firm based in the United Arab Emirates, has aspirations to become a trusted root certificate authority in one of the world’s most popular web browsers.